| CPC G06F 12/02 (2013.01) [G06F 12/14 (2013.01); H04L 9/0825 (2013.01)] | 20 Claims |
|
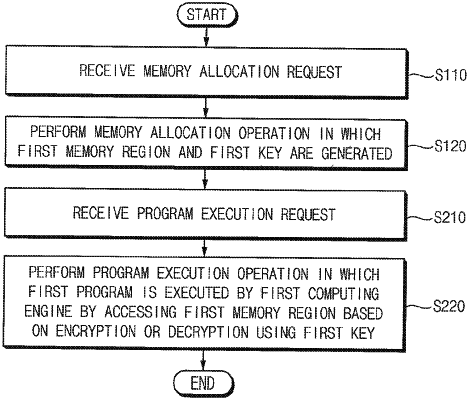
1. A method of allocating and protecting a memory in a computational storage device including a first computing engine and a buffer memory, the method comprising:
receiving a memory allocation request from a host device that is disposed outside the computational storage device;
based on the memory allocation request, performing a memory allocation operation in which a first memory region is generated in the buffer memory and a first key associated with the first memory region is generated;
receiving a program execution request from the host device; and
based on the program execution request, performing a program execution operation in which a first program is executed by the first computing engine by accessing the first memory region based on an encryption or a decryption using the first key,
wherein performing the program execution operation includes performing at least one of an encryption operation on write data to be stored in the first memory region and a decryption operation on read data to be retrieved from the first memory region using the first key, and
wherein performing at least one of the encryption operation and the decryption operation includes:
reading encrypted first data from the first memory region;
obtaining the first data by decrypting the encrypted first data using the first key;
obtaining second data by executing the first program based on the first data;
encrypting the second data using the first key to generate encrypted second data; and
storing the encrypted second data in the first memory region.
|