| CPC H04L 9/0861 (2013.01) [H04L 63/1416 (2013.01)] | 17 Claims |
|
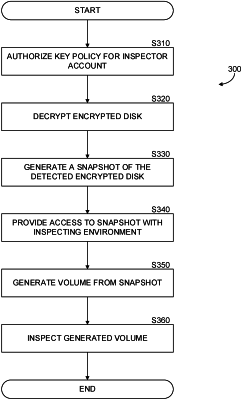
1. A method for reducing use of restricted operations in a cloud computing environment during cybersecurity threat inspection, comprising:
detecting an encrypted disk in a cloud computing environment, the encrypted disk encrypted utilizing a first key in a key management system (KMS);
generating a second key in the KMS, the second key providing access for a principal of an inspection environment;
generating a snapshot of the encrypted disk;
generating a volume based on the snapshot of the encrypted disk, wherein the volume is re-encrypted with the second key;
generating a snapshot of the re-encrypted volume;
generating an inspectable disk from the snapshot of the re-encrypted volume; and
initiating inspection for a cybersecurity object on the inspectable disk.
|