| CPC H04L 63/20 (2013.01) [G06F 18/22 (2023.01); G06F 18/24143 (2023.01); G06N 20/00 (2019.01); H04L 63/102 (2013.01)] | 20 Claims |
|
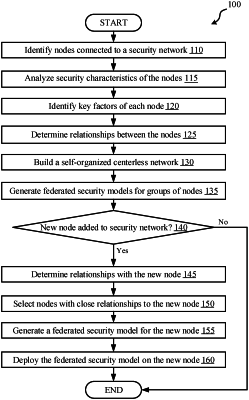
1. A computer-implemented method comprising:
identifying a plurality of nodes connected to a security network;
analyzing security characteristics of each node of the plurality of nodes, wherein the security characteristics comprise at least one of data regarding security policies and data regarding security server layers;
identifying, from the security characteristics, key factors for each node;
calculating similarities between each node of the plurality of nodes using the key factors;
building a self-organized centerless network across the plurality of nodes by grouping nodes based on the similarities between each node, resulting in groups of nodes; and
generating federated security models for the groups of nodes.
|