| CPC H04L 63/20 (2013.01) [H04L 63/1433 (2013.01); H04L 63/107 (2013.01)] | 20 Claims |
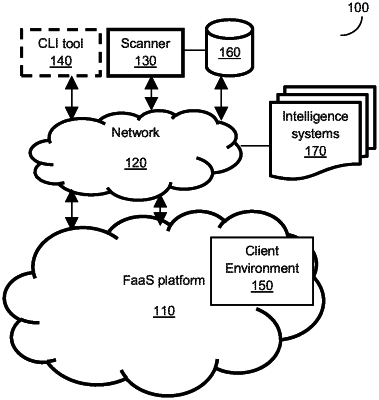
|
1. A method comprising:
based on analyzing a serverless function for which a first role is defined, identifying actual security permissions that the first role grants to the serverless function for access to a first resource;
generating a least privilege role for the serverless function that grants least privilege security permissions for access to the first resource based, at least in part, on a first attribute of the serverless function, wherein the least privilege security permissions comprise a set of minimal permissions for access to the first resource by the serverless function;
determining if the actual security permissions granted to the serverless function by the first role are less strict than the least privilege security permissions granted by the least privilege role based, at least in part, on comparing the least privilege security permissions with the actual security permissions; and
based on determining that the actual security permissions granted to the serverless function are less strict than the least privilege security permissions, reporting that the first role defined for the serverless function is over-permissive relative to the least privilege security permissions and performing a mitigation action for the serverless function.
|