| CPC H04L 63/1491 (2013.01) [G06F 9/547 (2013.01)] | 20 Claims |
|
1. A system comprising:
at least one hardware processor; and
a computer-readable medium storing instructions that, when executed by the at least one hardware processor, cause the at least one hardware processor to perform operations comprising:
identifying a first version of an application having a plurality of predefined endpoints, a predefined endpoint being a portion of the application that receives communications over a network via an interface;
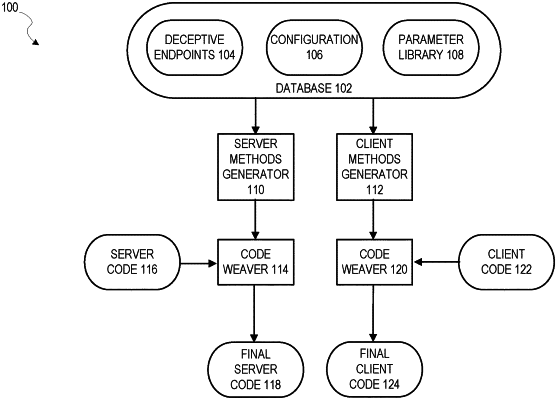
accessing a list of deceptive endpoints stored in a database, a deceptive endpoint being an endpoint not contained in the plurality of predefined endpoints;
accessing server code and client code stored in a parameter library in the database, the server code and client code stored in the parameter library defining functions not needed to run the first version of the application;
weaving the server code stored in the parameter library with server code of the first version of the application, using a configuration file stored in the database, the configuration file linking parameters defined in the list of deceptive endpoints with the server code stored in the parameter library, the weaving the server code including inserting parameters in the list of the deceptive endpoints that are linked to the server code;
weaving the client code stored in the parameter library with client code of the first version of the application, using the configuration file;
storing the weaved server code as a server-portion of a second version of the application and the weaved client code as a client-portion of the second version of the application;
loading the server-portion of the second version of the application into memory for execution; and
executing the server-portion of the second version of the application, causing deceptive traffic to be sent from a server to a client accessing a deceptive endpoint in the plurality of deceptive endpoints.
|