| CPC H04L 63/1433 (2013.01) | 17 Claims |
|
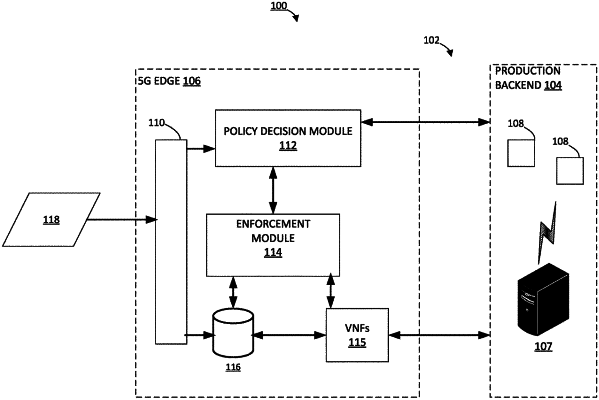
1. A computer-implemented method performed at an edge of a core network, the method comprising:
identifying an application that is connected to the core network;
extracting design attributes associated with one or more specifications of the application;
extracting implementation attributes associated with a code tool of the application;
monitoring the edge of the core network so as to identify monitored attributes associated with the application; and
comparing the design attributes, implementation attributes, and monitored attributes with one another so as determine whether there is an inconsistency between the design attributes, implementation attributes, and monitored attributes.
|