| CPC H04L 63/1416 (2013.01) [G06F 9/505 (2013.01); H04L 63/0435 (2013.01); H04L 63/0823 (2013.01); H04L 63/1425 (2013.01); H04L 67/1097 (2013.01)] | 13 Claims |
|
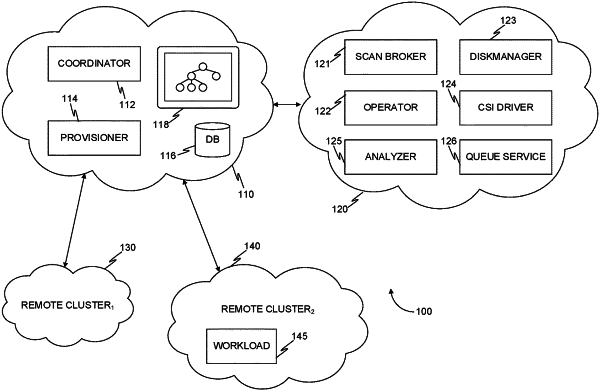
1. A method for scalable vulnerability detection, comprising:
selecting a workload of a plurality of workloads deployed in a first cloud environment for inspection, wherein the workload includes a first disk;
generating in a remote orchestration system an inspection node, the inspection node including an inspection disk, wherein the inspection node is provisioned in response to demand for an inspection node;
generating a volume on which the inspection disk is mounted, wherein the inspection disk is generated from the first disk;
providing access to the volume for the inspection node; and
inspecting the volume for an object, the object indicating a vulnerability.
|