| CPC H04L 63/108 (2013.01) [H04L 63/0807 (2013.01); H04L 63/083 (2013.01); H04L 2463/082 (2013.01)] | 20 Claims |
|
1. A system, the system comprising:
one or more processors; and
one or more computer-readable non-transitory storage media comprising instructions that, when executed by the one or more processors, cause one or more components of the system to perform operations comprising:
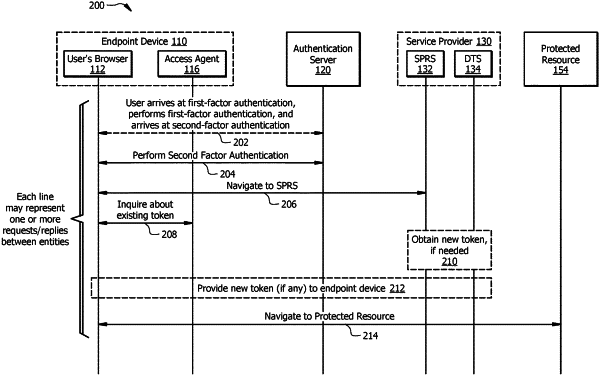
determining that an endpoint device has requested to discover a location of a protected resource, the protected resource protected by a gateway;
providing the endpoint device with a token based on the endpoint device successfully completing a first multi-factor authentication procedure, wherein the first multi-factor authentication procedure comprises authenticating a first authentication factor and a second authentication factor, the second authentication factor based on performing a real-time verification of a user of the endpoint device;
receiving the token from the endpoint device;
determining whether the token provided by the endpoint device is valid, the token indicating that the endpoint device successfully completed the first multi-factor authentication procedure in connection with accessing an authentication enforcement resource; and
permitting the endpoint device to discover the location of the protected resource based on determining that the endpoint device has provided the token that is valid.
|