| CPC H04L 63/0861 (2013.01) [H04L 9/3242 (2013.01); H04L 9/3247 (2013.01); H04L 63/0442 (2013.01); H04L 63/06 (2013.01); H04L 63/061 (2013.01); H04L 63/0807 (2013.01)] | 20 Claims |
|
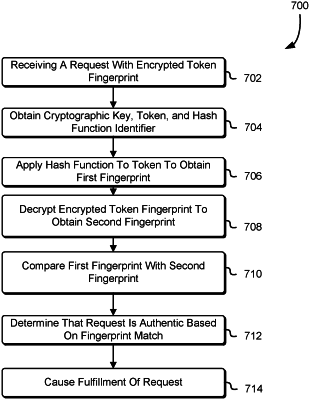
1. A computer-implemented method, comprising:
receiving, at a service of a computing resource service provider, a request with a token indicative of a registered network-addressable device of a customer, a digital signature associated with the token and signed by a private key of a public/private key pair, and an identifier registered by the customer of the computing resource service provider in association with a public key and associated with an authorizing mechanism usable to perform an operation on the token, the token comprising at least a credential useable to authenticate the registered network-addressable device;
determining, at the service and based at least in part on the identifier, the public key, of the public/private key pair, from a plurality of public keys, wherein the plurality of public keys are associated with a plurality of registered network-addressable devices;
verifying the digital signature based at least in part on the token and the public key; and
as a result of successful verification of the digital signature, performing an authorization routine to determine whether fulfillment of the request is authorized, the authorization routine including at least performing the operation on the token based, at least in part, on the authorizing mechanism associated with the identifier and performing a comparison process based on at least performing the operation on the token.
|