| CPC H04L 63/0281 (2013.01) [G06F 9/45558 (2013.01); H04L 63/062 (2013.01); H04L 63/083 (2013.01); G06F 2009/45587 (2013.01); G06F 2009/45595 (2013.01); H04L 2101/663 (2022.05)] | 20 Claims |
|
1. A system associated with a cloud computing environment, comprising:
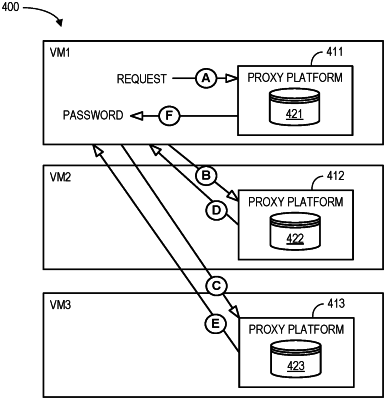
a proxy platform data store containing node data associated with nodes of the cloud computing environment, each node storing multi-party computation information including a partial password key, wherein each partial password key is generated as a mathematical part of a single password; and
a proxy platform able to access the proxy platform data store, including:
a computer processor, and
computer memory, coupled to the computer processor, storing instructions that, when executed by the computer processor cause the processor to:
(i) detect that a first node needs to access a cloud application secret key via receipt of a request from the first node including a first node partial password key, wherein each node stores a respective partial password key prior to the detection,
(ii) determine, based on information in the proxy platform data store, a set of nodes associated with the cloud application secret key that the first node needs to access,
(iii) generate the cloud application secret key in a secure enclave at the proxy platform, the generation via application of a multi-party computation algorithm to the multi-party computation information, the multi-party computation algorithm combining the multi-party computation information including the partial password keys received from each node in the set of nodes and the received first node partial password key; and
(iv) store the generated cloud application secret key in the secure enclave at the proxy platform for some period and then evict the generated cloud application secret key.
|