| CPC H04L 63/0245 (2013.01) [H04L 63/0263 (2013.01); H04L 47/20 (2013.01); H04L 63/145 (2013.01); H04L 63/20 (2013.01); H04L 67/14 (2013.01)] | 19 Claims |
|
1. A system, comprising:
a processor of a network device configured to:
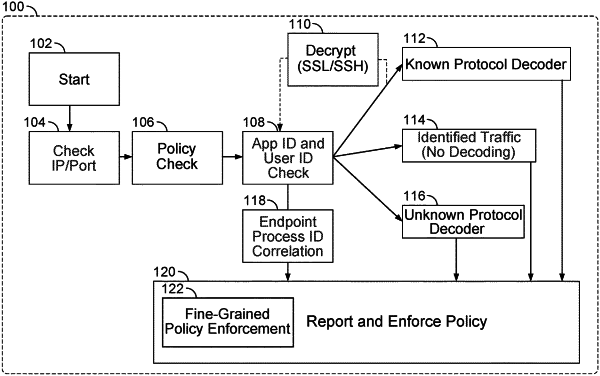
receive process identification (ID) information from an endpoint (EP) agent executed on an EP device on an enterprise network, wherein the process ID information identifies a process that is associated with a network session, wherein the network session is an outbound network session or an inbound network session on the EP device on the enterprise network, wherein the process ID information indicates that it is a known process, an unknown process, or a known but unexpected process, wherein the process ID information is stored as a digest of a file name of a binary/executable associated with the process that initiated the network session, and wherein the EP agent selected the network session for punting to the network device for inspection;
monitor network communications associated with the network session at the network device to identify an application identification (APP ID) for the network session; and
perform an action based on a security policy using the process ID information and the APP ID, wherein the security policy includes an EP security policy, wherein the EP agent implements the EP security policy to selectively punt the network session to the network device on the enterprise network, wherein the network device includes a firewall, wherein the security policy includes a fine-grained firewall policy, and wherein the firewall implements the fine-grained firewall policy; and
a memory coupled to the processor and configured to provide the processor with instructions.
|