| CPC G06Q 40/03 (2023.01) [G06Q 20/12 (2013.01); G06Q 20/24 (2013.01); G06Q 20/4016 (2013.01); G06Q 40/02 (2013.01); G06Q 50/01 (2013.01)] | 17 Claims |
|
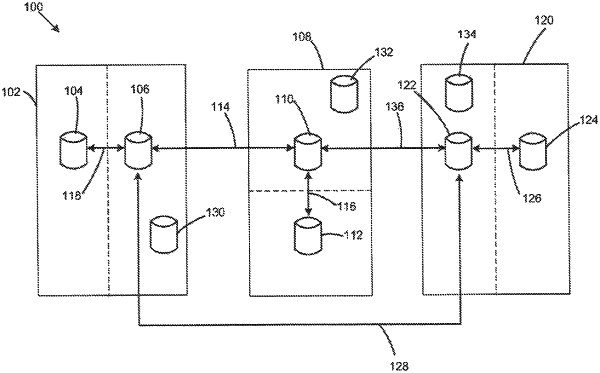
1. A method, comprising:
identifying a network address, a port number, and a security protocol of a network node from among a plurality of computing nodes in a lookup table of a computing device;
establishing a secure network channel between the computing device and a data store of the network node based on the identified network address, the port number, and the security protocol;
receiving, by the computing device, stock keeping unit (SKU) data from the network node via a data exchange over the established secure network channel;
correlating, by the computing device, the SKU data with previous purchases of a user;
generating, by the computing device, a profile for the user which includes the correlated previous purchases of the user;
receiving, by the computing device, a request for approval of a transaction from the user;
generating, by the computing device, a conformance score for the transaction based on a comparison of the transaction with the correlated purchases in the profile; and
denying, by the computing device, the transaction based on the conformance score indicating that the transaction is nonconforming;
wherein the request for the approval is determined to be fraudulent based at least in part on a comparison between data related to the transaction and a geographic location based on a Global Positioning System reading associated with the request.
|