| CPC G06F 21/6245 (2013.01) [G06F 16/9024 (2019.01); G06F 16/906 (2019.01)] | 22 Claims |
|
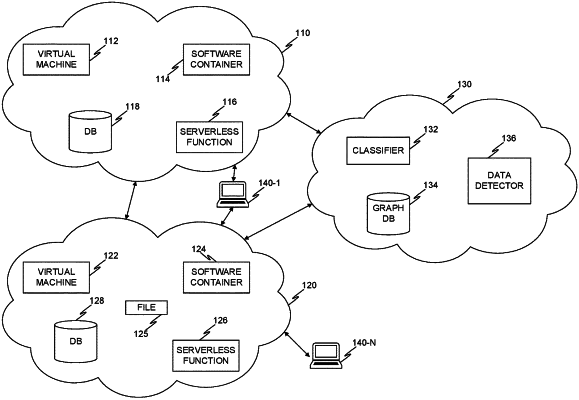
1. A method for agentless detection of sensitive data in a cloud computing environment and rendering the same for display, comprising:
detecting a first data object in a first cloud computing environment, the first data object including a data schema and content;
detecting a second data object in a second cloud computing environment, the second cloud computing environment associated with the first cloud computing environment, the second data object having the data schema of the first data object, wherein the first data object and the second data object are generated based on the data schema, the data schema including a plurality of integrity constraints;
generating in a security graph hosted on a graph database: a first data object node representing the first data object, a second data object node representing the second data object, and a data schema node representing the data schema, wherein the security graph further includes a representation of the first cloud computing environment;
storing a classification based on the content in the security graph, wherein the content is classified as either sensitive data or non-sensitive data;
rendering an output based on the classification and the data schema node, in lieu of the first data object node and the second data object node, in response to receiving a query to detect a node representing a data object classified as sensitive data;
generating a first cluster node in the security graph, the first cluster node representing a plurality of data objects having a shared data schema, each data object represented by a node in the security graph, wherein each data object is deployed in the cloud computing environment; and
generating a second cluster node in the security graph, the second cluster node representing a second plurality of data objects having the shared data schema, each data object represented by a node in the security graph, wherein each data object is deployed in another cloud computing environment, associated with the cloud computing environment.
|