| CPC G06F 21/602 (2013.01) [G06F 9/5016 (2013.01); G06F 21/6227 (2013.01); G06N 20/00 (2019.01)] | 20 Claims |
|
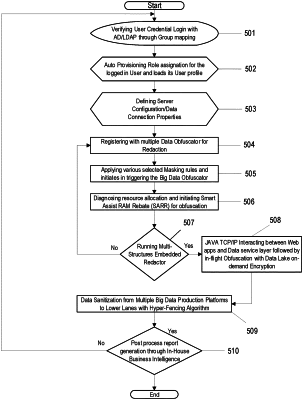
1. A computer-implemented method of resource allocation and rebating during in-flight data masking and on-demand encryption of big data on a network comprising the steps of:
authenticating, by an obfuscation computer machine, a request for a big data dataset based on credentials received from a source,
said obfuscation computer machine coupled to the network,
said obfuscation computer machine containing computer-readable memory,
said request stored in a first sector of the computer-readable memory;
said big data dataset stored in a data store coupled to the network, said big data dataset including sensitive information and non-sensitive information;
auto provisioning, by the obfuscation computer machine, a profile corresponding to the request, said profile stored in a second sector of the computer-readable memory;
assigning, by the obfuscation computer machine, access rights for the request based on the profile, said access rights stored in a third sector of the computer-readable memory;
defining, by the obfuscation computer machine, server configuration and data connection properties for the data store containing the big data dataset, said server configuration and said data connection properties stored in a fourth sector of computer-readable memory;
establishing, by the obfuscation computer machine, a secure connection from the obfuscation computer machine to the data store based on the server configuration and the data connection properties;
registering, by the obfuscation computer machine, at least one multiple data obfuscation type stored in a fifth sector of computer-readable memory;
loading, by the obfuscation computer machine into a sixth sector of computer-readable memory, the big data dataset from the data store on the network;
searching, by the obfuscation computer machine, the big data dataset for the sensitive information to be redacted;
redacting into a sanitized dataset, by the obfuscation computer machine, the sensitive information in the big data dataset based on said at least one multiple data obfuscation type and the non-sensitive information;
storing, by the obfuscation computer machine into a seventh sector of computer-readable memory, the sanitized dataset;
encrypting, by the obfuscation computer machine, the sanitized dataset into encrypted data, said encrypted data stored in an eighth sector of computer-readable memory; and
transmitting, by the obfuscation computer machine, the encrypted data in response to the request.
|