| CPC G06F 21/60 (2013.01) [G06F 21/54 (2013.01); G06F 21/78 (2013.01)] | 20 Claims |
|
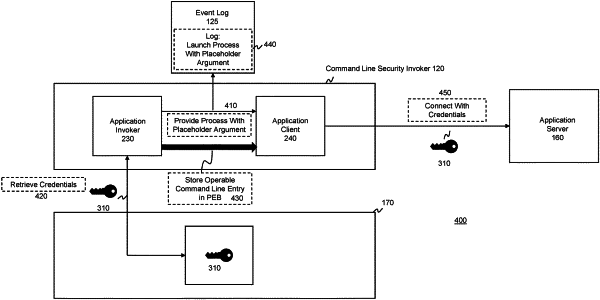
1. A computer-implemented method for securing the use of command line entries, the method comprising:
invoking, by a main process, a secondary process in a computing environment in a suspended mode;
providing one or more placeholder command line entry to the secondary process;
retrieving at least one secret by the main process; and
storing an operable command line entry in a memory location associated with the secondary process, wherein the one or more placeholder command line entry is nullified; and
wherein the secondary process is configured to process the operable command line entry and use the at least one secret.
|