| CPC G06F 21/577 (2013.01) [G06F 2221/033 (2013.01)] | 18 Claims |
|
1. A method comprising:
receiving, from a target repository, a set of source code from a first operating environment;
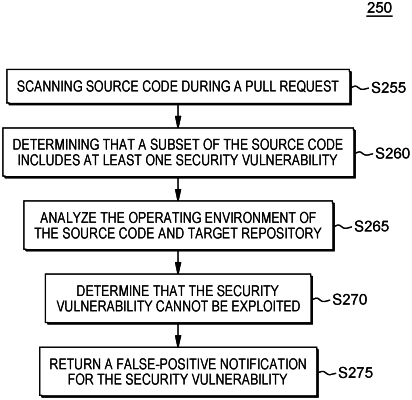
scanning, during a pull request of the target repository, the set of source code;
determining, by a security determination module, that a first subset of the source code includes a security vulnerability;
analyzing the first operating environment for the set of source code and the target repository, with the analysis including determining whether the first operating environment for the set of source code and the target repository have a set of storage device controllers that are structured and configured to support the set of source code and the target repository;
responsive to the analysis of the first operating environment, determining that the security vulnerability of the first subset of the source code cannot be exploited;
responsive to the determination, returning a false positive notification for the security vulnerability; and
setting up a trigger for invalidating a false positive based, at least in part, on which group of false positives is invalidated, the trigger for invalidating the false positive being set up in order to reduce a time spent re-analyzing false positives, the trigger for invalidating the false positive, during a next scan, unmarking the false positive and forcing a scanner to check again for false positives.
|