| CPC G06F 21/577 (2013.01) [G06F 21/552 (2013.01); G06F 21/554 (2013.01); G06F 21/566 (2013.01); G06F 21/6227 (2013.01); G06N 5/04 (2013.01); G06N 20/00 (2019.01); H04L 63/102 (2013.01); H04L 63/1425 (2013.01); H04L 63/1433 (2013.01); H04L 63/1441 (2013.01); G06F 2221/033 (2013.01); G06F 2221/034 (2013.01)] | 20 Claims |
|
1. A computer-implementable method for performing a security operation, comprising:
monitoring an entity, the monitoring observing at least one electronically-observable data source, the monitoring comprising monitoring at least one of a plurality of electronically-observable actions via a protected endpoint;
deriving an observable based upon the monitoring of the electronically-observable data source;
identifying a security related activity of the entity, the security related activity being based upon the observable derived from the electronic data source, the security related activity being of analytic utility;
associating the security related activity with a session;
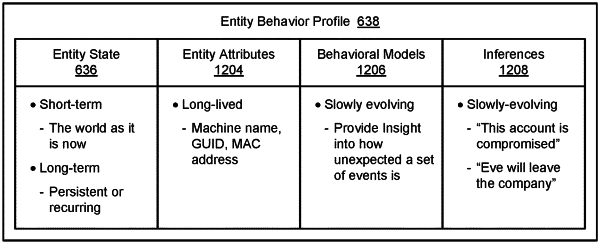
processing an entity behavior profile of the entity and contextual information relating to the entity to generate an inference regarding the entity;
generating an entity behavior profile element based upon the security related activity and the session; and,
performing the security operation via the protected endpoint and a security analytics system, the security operation using the entity behavior entity behavior profile element and the inference regarding the entity, the security analytics system executing on a security analytics system hardware processor.
|