| CPC G06F 21/566 (2013.01) [G06F 2221/034 (2013.01); G06F 2221/2125 (2013.01)] | 15 Claims |
|
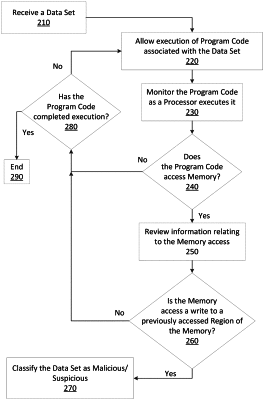
1. A method for analyzing computer data, the method comprising:
allowing instructions of a set of computer data to be executed by a processor;
monitoring actions performed by the execution of the instructions of the set of computer data, the monitoring performed by the processor executing a set of instrumentation code instructions;
pausing execution of the instructions of the computer data based on an identification that the monitored actions include writing data to a memory;
identifying that the monitored actions correspond to an access pattern of the memory that includes allocating a portion of the memory and includes invocation of an operating system program function, wherein the data written to the memory is written to a newly allocated memory portion;
comparing a signature generated from the data written to the allocated memory portion of the memory to a malware signature generated from previously identified malicious code; and
performing a corrective action based on an identification that the generated signature matches the malware signature.
|