| CPC G06F 21/31 (2013.01) [G06F 9/54 (2013.01); G06F 13/4068 (2013.01); G06F 21/572 (2013.01); G06F 21/85 (2013.01)] | 15 Claims |
|
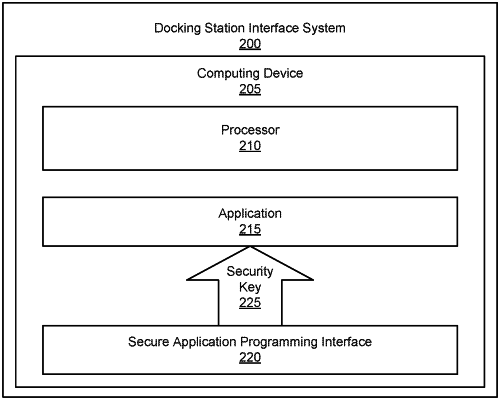
1. A method of selectively securing a computing device at a docking station, comprising:
creating a security key between a security application programming interface (API) and an application executed on the computing device;
upon logging into and execution of a basic input/output system (BIOS) of the computing device by a user, registering the application with the security API using the security key;
upon receiving a first request to remove the computing device from the docking station;
validating first authorization of the user to remove the computing device from the docking station using first settings associated with the application, wherein the first settings associated with the application include conditions associated with removing the computing device from the docking station;
upon validating the first authorization of the user to remove the computing device from the docking station, determining that the conditions associated with removing the computing device from the docking station have been satisfied; and
upon determining that the conditions associated with removing the computing device from the docking station have been satisfied, enabling removal of the computing device from the docking station; and
upon receiving a second request to access a universal serial bus (USB) port associated with the computing device;
validating second authorization of the user to access the USB port using second settings associated with the application, wherein the second settings associated with the application include conditions associated with accessing the USB port;
upon validating the second authorization of the user to access the USB port, determining that the conditions associated with accessing the USB port have not been satisfied; and
upon determining that the conditions associated with accessing the USB port have not been satisfied, disabling access to the USB port.
|