| CPC H04W 68/005 (2013.01) [H04L 63/107 (2013.01); H04L 63/20 (2013.01); H04L 67/52 (2022.05); H04W 4/029 (2018.02); H04W 24/08 (2013.01); G10L 17/00 (2013.01); G10L 17/06 (2013.01); H04L 65/1083 (2013.01); H04L 67/303 (2013.01); H04L 67/53 (2022.05); H04M 1/72463 (2021.01)] | 11 Claims |
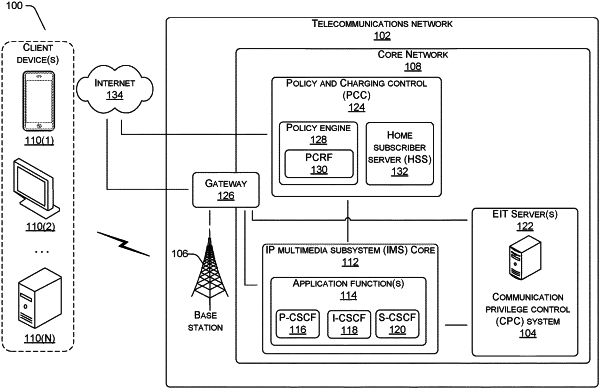
|
1. A computer-implemented method, comprising:
retrieving a set of communication privilege rules that are for a control of real-time communications associated with a client account and that include a grey-list of contacts with whom a secondary account holder (SAH) of the client account is permitted limited communications based on a set of conditions that includes a geolocation of an SAH device associated with the SAH;
detecting a real-time communication session between the SAH device and a third-party device;
retrieving, from the SAH device, session metadata that includes a third-party identifier and the geolocation of the SAH device;
based at least in part on the grey-list of contacts and the session metadata, determining that the real-time communication session is restricted by the set of communication privilege rules;
selecting a trusted device to intercept the real-time communication session; and
causing the SAH device to re-direct the real-time communication session from the SAH device to the trusted device.
|