| CPC H04L 63/1491 (2013.01) [G06F 21/566 (2013.01); H04L 41/12 (2013.01); H04L 61/4505 (2022.05); H04L 61/5007 (2022.05); H04L 61/4523 (2022.05)] | 20 Claims |
|
1. A method comprising:
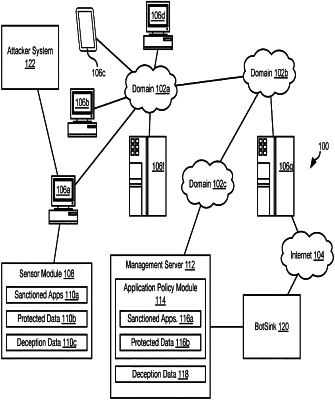
configuring, by a computer system, a system call to refer to a detour function;
receiving, by the computer system, the system call to the detour function from a source to obtain information regarding a remote network resource;
determining, by the computer system via the detour function, that the source is not on a list of sanctioned applications; and
in response to determining that the source is not on the list of sanctioned applications, returning, by the computer system via the detour function, a response to the system call having the information regarding the remote network resource replaced with information regarding a decoy server.
|