| CPC H04L 63/1433 (2013.01) [G06N 5/025 (2013.01); H04L 63/102 (2013.01); H04L 67/535 (2022.05)] | 16 Claims |
|
1. A computer-implemented method for providing automated actions in handling security threats, the method comprising:
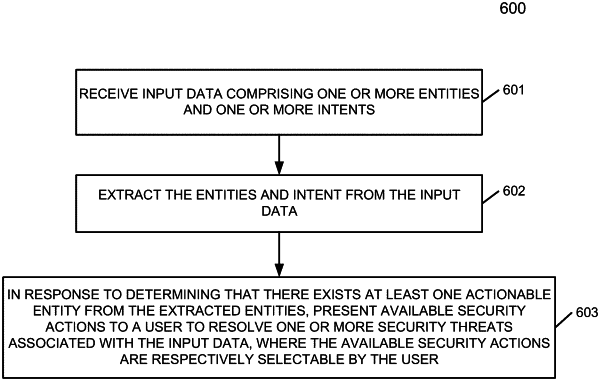
receiving input data comprising one or more entities and one or more intents;
extracting the entities and the intents from the input data;
traversing a data structure to determine whether there exists a connection between the extracted entities and the extracted intents, wherein the connection automatically triggers invocation of at least one specific action; and
in response to determining that there exists a connection between the extracted entities and the extracted intents, invoking the at least one specific action comprising:
presenting a plurality of available security actions to a user to resolve one or more security threats associated with the input data when there exists at least one actionable entity from the extracted entities, the available security actions being respectively selectable by the user;
presenting to the user respective confidence scores associated with the plurality of available security actions, wherein the confidence scores correspond with a range of security actions among the plurality of available security actions ranging from a mostly selected security action to a least selected security action;
in response to selecting an available security action by the user, automating a performance of the selected security action, without the user's input, to resolve the one or more security threats; and
dynamically updating the presented available security actions.
|