| CPC H04L 63/1433 (2013.01) [H04L 63/20 (2013.01)] | 20 Claims |
|
1. A computer-implemented method comprising:
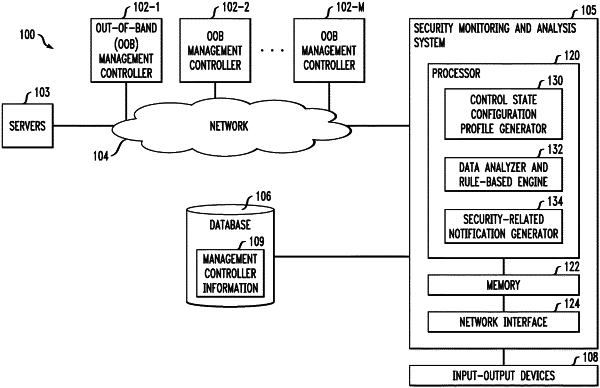
generating one or more control state configuration profiles for one or more hardware components of at least one out-of-band server management controller, wherein each control state configuration profile comprises hardware component identification information and configuration state information;
collecting data from the at least one out-of-band management controller via one or more interfaces;
analyzing the collected data by comparing the collected data to the one or more control state configuration profiles and applying at least one rule-based engine to the collected data, wherein applying the at least one rule-based engine to the collected data comprises identifying one or more firmware anomalies and one or more hardware anomalies attributed to one or more end-user devices coupled to at least one server coupled to the at least one out-of-band server management controller, by processing at least a portion of the collected data using one or more rules of the at least one rule-based engine;
generating an output comprising a notification of one or more security vulnerabilities, related to at least a portion of the one or more firmware anomalies and the one or more hardware anomalies, associated with the at least one out-of-band server management controller based at least in part on the comparing of the collected data to the one or more control state configuration profiles and the applying of the at least one rule-based engine to the collected data, wherein the one or more security vulnerabilities associated with the at least one out-of-band server management controller comprise one or more security vulnerabilities attributed to at least a portion of the one or more end-user devices coupled to the at least one server coupled to the at least one out-of-band server management controller;
automatically disabling at least a portion of the one or more end-user devices in response to the notification of one or more security vulnerabilities; and
providing at least a portion of the output to one or more enterprise security information event management tools, wherein providing the at least a portion of the output to the one or more enterprise security information event management tools comprises configuring at least a portion of the one or more enterprise security information event management tools with one or more rules, based at least in part on the at least a portion of the output, to classify at least one of one or more device attributes and one or more device settings as one or more security vulnerabilities in the one or more enterprise security information event management tools;
wherein the method is performed by at least one processing device comprising a processor coupled to a memory.
|