| CPC H04L 63/1425 (2013.01) | 14 Claims |
|
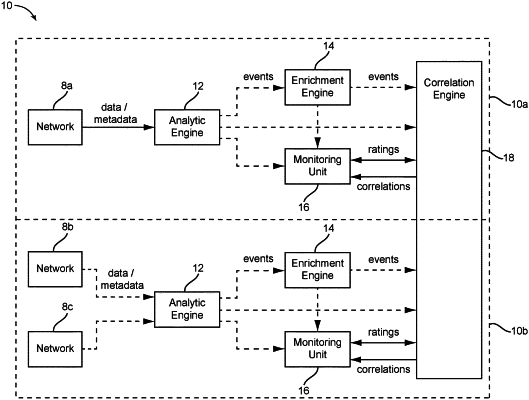
1. A method of analyzing cybersecurity events in at least one network environment in real time comprising steps of:
receiving, in real time, data originating from the at least one network environment;
processing, in real time, the received data producing a plurality of events in response to the processing;
normalizing and transforming features of the plurality of events into a single representative feature type;
creating feature hashes as a function of feature vectors comprising using multiple hashing functions that preserve locality of feature vectors;
inserting the plurality of events and corresponding feature vectors into a hash table;
finding candidate correlated events comprising looking up events having a prescribed similarity metric in the hash table;
storing the candidate correlated events having been found in a data store.
|