| CPC H04L 63/0263 (2013.01) [G06F 16/282 (2019.01); H04L 43/12 (2013.01); H04L 63/10 (2013.01); H04L 63/1408 (2013.01); H04L 67/1095 (2013.01)] | 20 Claims |
|
1. A computer readable storage device or storage disk comprising computer readable instructions to cause at least one processor circuit to at least:
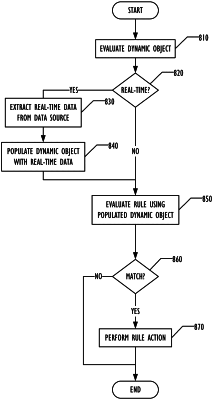
populate a first dynamic object of a firewall rule with first information to identify a first updateable set of devices that satisfy a first one of a plurality of conditions associated with the firewall rule, the first information based on first data obtained from an appliance that is to monitor communication traffic in at least a portion of a network;
populate a second dynamic object of the firewall rule with second information to identify a second updateable set of devices that satisfy a second one of the plurality of conditions associated with the firewall rule, the second information based on second data obtained from a data source different from the appliance; and
apply, based on evaluation of the first dynamic object and the second dynamic object, the firewall rule to first network traffic associated with a first device in communication with the network, the firewall rule to cause the first network traffic to be at least one of blocked, permitted, rate limited, quarantined or captured.
|