| CPC G06N 3/08 (2013.01) [G06F 18/24 (2023.01); G06Q 20/3825 (2013.01); G06V 10/82 (2022.01); G06V 30/19147 (2022.01); G06V 30/19173 (2022.01); G06V 30/226 (2022.01); G06V 40/33 (2022.01); G06N 3/04 (2013.01)] | 20 Claims |
|
1. A method, comprising:
receiving, by a device, information indicating names of individuals;
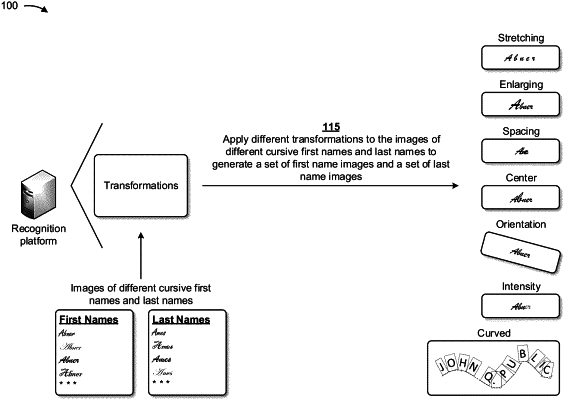
applying, by the device, different cursive fonts to each of the names to generate images of different cursive names;
applying, by the device, transformations to the images of the different cursive names to generate a set of images,
wherein a transformation, of the transformations, transforms a straight line portion of contiguous characters of a name, of the different cursive names, to follow a curve rather than a straight line;
training, by the device, a neural network model, with the set of images, to generate a trained neural network model;
receiving, by the device, an image of a signature,
wherein the signature is associated with a name of the names;
permitting or denying access, by the device using the trained neural network model, to another device based on the name associated with the signature; and
performing a transaction based on permitting or denying access to the other device.
|