| CPC G06F 21/602 (2013.01) [G06F 21/604 (2013.01); G06F 21/6227 (2013.01)] | 20 Claims |
|
1. A method for providing a personal data storage service between a first user who is a data provider and a second user who is a data requester by using a smart contract based on a first layer and a privacy layer and a storage layer based on a second layer, comprising steps of:
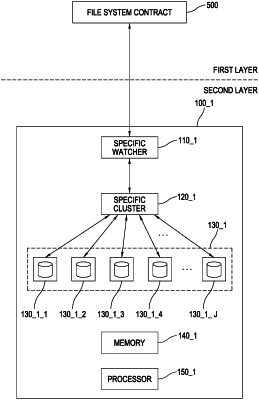
(a) (i) on condition that a plurality of partial re-encryption keys generated from a re-encryption key have been recorded in a distributed manner in a plurality of PRE (proxy re-encryption) nodes included in the privacy layer in response to the re-encryption key being generated by using a second public key of the second user and a first private key of the first user through a first user terminal of the first user interlocked with the privacy layer according to data access request information from a second user terminal of the second user, wherein the re-encryption key is a key capable of converting a first encoded encryption key to be made by encoding an encryption key with a first public key of the first user into a second encoded encryption key to be made by encoding the encryption key with the second public key of the second user and (ii) on condition that (ii-1) subject data has been acquired, (ii-2) encoded subject data has been acquired by applying the encryption key to the subject data, and (ii-3) the first encoded encryption key has been generated by applying the first public key of the first user to the encryption key, through the first user terminal interlocked with the storage layer, acquiring, by a specific storage node included in the storage layer, the first encoded encryption key and the encoded subject data; and
(b) in response to (i) the first encoded encryption key and the second public key being transmitted to the PRE nodes, (ii) second encoded encryption key pieces being generated by using the first encoded encryption key, the second public key, and a specific cardinal number of specific partial re-encryption keys recorded in specific PRE nodes among the PRE nodes, (iii) the second encoded encryption key pieces being transmitted to the second user terminal, (iv) the second encoded encryption key being generated from the second encoded encryption key pieces by the second user terminal, and (v) the encryption key being acquired by applying a second private key of the second user to the second encoded encryption key, instructing, by the specific storage node, the second user terminal to acquire the subject data by applying the encryption key to the encoded subject data transmitted to the second user terminal.
|