| CPC G06F 21/577 (2013.01) [G06F 9/45558 (2013.01); G06F 9/5072 (2013.01); G06F 9/5077 (2013.01); G06F 16/288 (2019.01); G06F 2009/4557 (2013.01); G06F 2009/45587 (2013.01); G06F 2009/45595 (2013.01)] | 19 Claims |
|
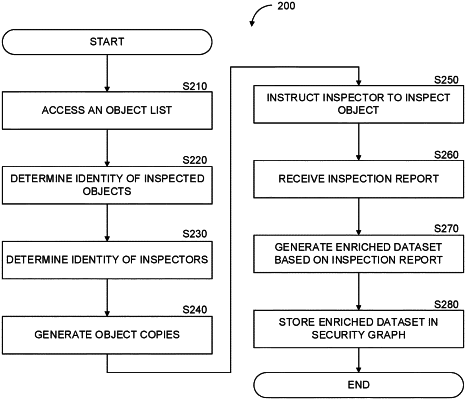
1. A method for remote inspection of a cloud computing environment for a cybersecurity object, comprising:
accessing a first cloud computing environment, the first cloud computing environment including a plurality of workloads;
generating a copy from a workload of the plurality of workloads in a second cloud computing environment;
selecting an inspector based on an identity of the inspector, the identity corresponding to a cybersecurity object;
initiating inspection for the cybersecurity object in the copy of the workload by the inspector;
detecting the cybersecurity object in the copy of the workload;
sending an identifier of the detected cybersecurity object and an identifier of the workload to an inspection environment, wherein the inspection environment is configured to store the identifier of the detected cybersecurity object and the identifier of the workload in a security database;
detecting the cybersecurity object in a copy of a second workload of the plurality of workloads;
performing a graph-based analysis to generate an enriched dataset based on the cybersecurity object;
generating in the inspection environment: a representation of the cybersecurity object, a representation of the workload, and a representation of the second workload;
connecting in the security database the representation of the cybersecurity object, based on the graph-based analysis, to: the representation of the workload and the representation of the second workload; and
using a result of the graph-based analysis to detect a vulnerability in the workload.
|