| CPC G06F 21/577 (2013.01) [H04L 9/0643 (2013.01); G06F 2221/034 (2013.01)] | 32 Claims |
|
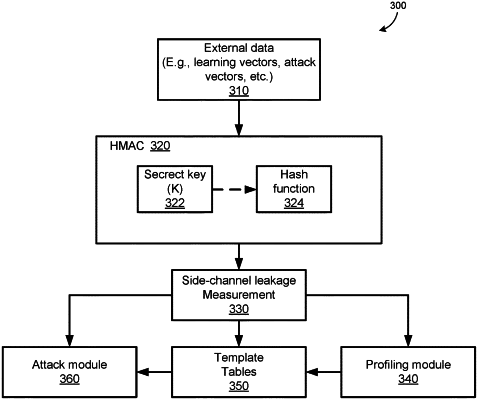
1. A method for testing for vulnerability of an implementation of a hash-based message authentication code (HMAC) algorithm to a side-channel attack, the method comprising:
mounting a template attack on a hash function used to implement the HMAC algorithm, the template attack including:
generating, based on first side-channel leakage information associated with execution of the hash function, a plurality of template tables, each template table of the plurality of template tables corresponding, respectively, with a subset of bit positions of an internal state of the hash function; and
generating, based on a comparison of second side-channel leakage information with the plurality of template tables, a plurality of hypotheses for an internal state of an invocation of the hash function based on a secret key;
generating, using the hash function, respective hash values generated from each of the plurality of hypotheses and a message;
comparing each of the respective hash values with a hash value generated using the secret key and the message; and
based on the comparison, determining vulnerability of the HMAC algorithm based on a hash value of the respective hash values matching the hash value generated using the secret key and the message.
|