| CPC G06F 21/52 (2013.01) [G06F 11/3668 (2013.01); G06F 21/51 (2013.01); G06F 21/562 (2013.01); G06F 21/566 (2013.01); G06F 21/577 (2013.01); G06F 2221/033 (2013.01); H04L 67/12 (2013.01)] | 20 Claims |
|
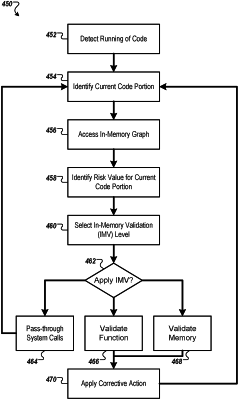
1. A method for hardening network-accessible controllers through integrating a customized security layer, the method comprising:
identifying computer-readable code configured to be run on a particular controller, wherein the computer-readable code is configured to be stored in a memory in a plurality of code portions, each code portion comprising one or more instructions to be performed by the particular controller;
identifying contextual information associated with the particular controller;
identifying a specific code portion from the plurality of code portions that is configured to be run on the particular controller;
selecting, from a plurality of available flow control integrity (IMV) schemes, an IMV scheme based on the identified contextual information, wherein the selected IMV scheme specifies instructions for at least one of:
function validation, or
memory address verification;
applying the selected IMV scheme to the identified specific code portion; and
hardening the particular controller by deploying the specific code portion to run on the particular controller according to the applied IMV scheme.
|