| CPC H04W 12/106 (2021.01) [H04W 12/121 (2021.01); H04W 28/065 (2013.01)] | 16 Claims |
|
1. An apparatus for traffic security processing in a slicing service of mobile edge computing, the apparatus comprising:
a plurality of security modules for analyzing a received packet to respectively execute security functions suitable for slicing security of mobile edge computing;
a controller for managing a slicing security module list in the mobile edge computing; and
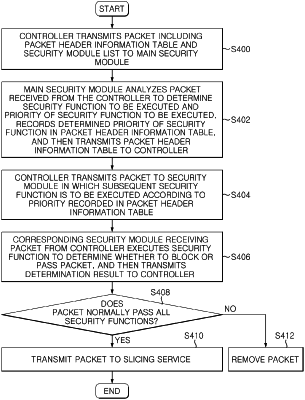
a main security module for analyzing a received packet on the basis of the slicing security module list to determine a security function to be executed and priority of the security function to be executed,
wherein the controller transmits the received packet to at least one corresponding security module among the plurality of security modules according to the priority of the security function to be executed, which is determined by the main security module,
wherein the controller receives a packet through a network interface card, generates a packet header information table and inserts the same to the front of a header of the packet, and transmits the packet header information table, packet information comprising the packet, and the slicing security module list to the main security module, and
wherein the main security module receives the packet header information table, the packet information comprising the packet, and the slicing security module list from the controller, analyzes the packet to determine the at least one security function to be executed and the priority of the at least one security function to be executed, records the determined priority of the security function in the packet header information table, and then transmits the packet header information table to the controller.
|