| CPC H04L 9/3278 (2013.01) [H04L 9/0822 (2013.01); H04L 9/085 (2013.01); H04L 9/321 (2013.01); H04L 9/3242 (2013.01)] | 15 Claims |
|
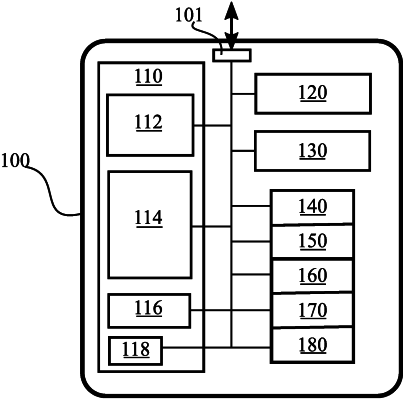
1. A cryptoprocessor comprising:
physical unclonable function circuitry comprising at least one physical unclonable function, and
at least one processing core configured to:
issue a request for a challenge to a server;
receive the challenge from the server;
provide the challenge as input to the physical unclonable function circuitry to derive a response to the challenge;
use the response as a first encryption key to encrypt a second encryption key;
cause the encrypted second encryption key to be provided to a the server;
use the second encryption key to establish a secure end-to-end connection with a correspondent party distinct from the server, and
wherein the cryptoprocessor is configured to decrypt an encryption key of the correspondent party with a second response as a key to obtain the encryption key of the correspondent party, the second response obtained from the physical unclonable function circuitry using a second challenge as input.
|