| CPC H04L 9/3247 (2013.01) [H04L 9/0825 (2013.01); H04L 9/14 (2013.01); H04L 9/3236 (2013.01)] | 20 Claims |
|
1. A system comprising:
a first device comprising:
a first general computing environment comprising:
a first communication interface;
a first memory storing first computer-executable instructions; and
a first processor in communication with the first communication interface and the first memory, the first processor executing the first computer-executable instructions to:
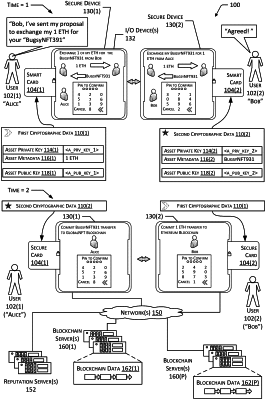
receive, from a first secure computing environment, a first invoice identifier;
determine first proposal data comprising:
a first asset public key,
the first invoice identifier,
a second asset public key,
data indicative of a condition whereby a first asset private key is sent and a second asset private key is received, and
a first device public key;
send, using the first communication interface, the first proposal data to a second device;
receive, using the first communication interface, signed second proposal data comprising:
second proposal data indicative of acceptance of the first proposal data, and
a first digital signature of the second proposal data that is signed by the second device;
send the signed second proposal data to the first secure computing environment; and
send signed first transfer data to the second device using the first communication interface; and
the first secure computing environment comprising:
a first secure encrypted memory storing:
a first device private key, and
the first asset private key;
a second memory storing second computer-executable instructions; and
a second processor in communication with: the first processor, the first secure encrypted memory, and the second memory, the second processor executing the second computer-executable instructions to:
determine first invoice data comprising the first invoice identifier (ID) and a first invoice key;
determine the signed second proposal data is validly signed;
establish a secure channel with a second secure computing environment of the second device;
determine the first secure computing environment and the second secure computing environment are associated with a common authority;
send, using the secure channel, the first invoice data to the second device;
receive, using the secure channel, second invoice data, wherein the second invoice data comprises:
a second invoice identifier, and
a second invoice key;
determine first transfer data comprising:
the first invoice identifier,
a first hash of at least a portion of the second proposal data, and
first encrypted data, encrypted using the first invoice key, the first encrypted data comprising the first asset private key;
determine the signed first transfer data by digitally signing the first transfer data using the first device private key; and
send the signed first transfer data to the first general computing environment.
|