| CPC H04L 9/3247 (2013.01) [G06F 11/3476 (2013.01); H04L 9/30 (2013.01)] | 19 Claims |
|
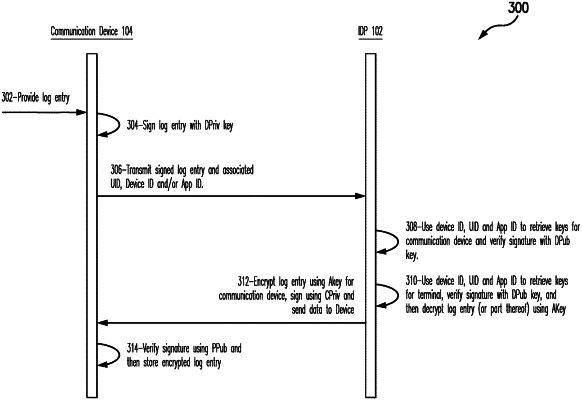
1. A computer-implemented method for use in appending one or more log entries to a data structure, the method comprising:
receiving, at a communication device, a log entry from a terminal;
signing, by the communication device, the log entry with a private key of a key pair specific to the communication device;
transmitting the signed log entry to an identity provider (IDP);
receiving, by the communication device, from the IDP, a signed, encrypted log entry;
verifying, by the communication device, a signature of the signed, encrypted log entry based on a public key associated with a key pair specific to the IDP;
appending the encrypted log entry to a digital identity included in the communication device;
transmitting the encrypted log entry to the IDP in response to an input indicative of a request from a relying party;
receiving, from the IDP, a second signed, encrypted log entry;
verifying, by the communication device, a signature of the second signed, encrypted log entry based on the public key associated with the key pair specific to the IDP; and
decrypting the second signed, encrypted log entry with the private key of the key pair specific to the communication device.
|