| CPC H04L 9/3073 (2013.01) [G06K 19/06037 (2013.01); H04L 9/0866 (2013.01); H04L 63/123 (2013.01); H04L 9/50 (2022.05)] | 18 Claims |
|
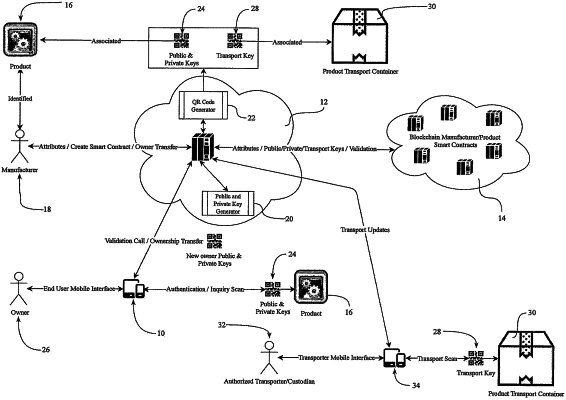
1. A method in support of creating public and private keys to be generated to a quick response (QR) code, near field communication (NFC) device, or other identifying media that can be readable, performed by one or more servers, using a decentralized blockchain technology, with the one or more servers being connected to a network and having memory, one or more processors, and one or more code sets stored in the memory and executable in the one or more processors, the method comprising the steps of:
receiving, by the one or more processors, first product information for a product from a manufacturer to be associated with a QR code, NFC device, or other identifying media;
allocating, by the one or more processors, a product entry record for the product identified by the manufacturer into a product smart contract or other transaction protocol;
receiving, by the one or more processors, manufacturing details of the product, the manufacturing details including at least one of a registration key, a serial number, manufacturer identifier, and a place of origin;
generating, by the one or more processors, a public key and private key associated with the product that are configured to be used by the manufacturer in the authentication of the product managed by the product smart contract or other transaction protocol;
receiving, by the one or more processors, an authentication pairing of the public key and the private key, both public and private key data for the public key and private key being populated into the product smart contract or other transaction protocol so that the public and private key data in the product smart contract or other transaction protocol is configured to be used for later validation;
providing, by the one or more processors, the public key and the private key from the manufacturer to be affixed to the same product with some media using the QR code, NFC device, or other identifying media;
providing, by the one or more processors, a first phase of product ownership assigned to the manufacturer;
recording, by a blockchain ecosystem, the manufacturing and product details contained within the product smart contract, including an encrypted form of the public key and the private key;
receiving, at the one or more processors, a private inquiry using the public key and the private key generated by the manufacturer, associated to the product, with an authentication call setting;
verifying, by the one or more processors, based on the public key and the private key, a look up to the product smart contract or other transaction protocol based on the key pairing provided, both the public and private key being transmitted to the product smart contract or other transaction protocol during verification;
generating, by the one or more processors, a decentralized call to validate the public key and the private key with both the public and private key data in the product smart contract or other transaction protocol;
verifying, by the blockchain ecosystem having a blockchain ledger, a valid transaction based on the public key and the private key and the associated product smart contract or other transaction protocol for the manufactured product;
recording, by the one or more processors, a valid authentication transaction to the blockchain ledger;
locking, by the one or more processors, the product smart contract or other transaction protocol from any further processing with respect to the product after the valid authentication transaction is recorded so as to prevent any future product authentication for the product;
transmitting by the one or more processors, a verification message to a claimant of the private key regarding authentication; and
generating, by the one or more processors, a second phase of product ownership that is allocated to the claimant as the owner of the public and the private key used in authentication.
|