| CPC H04L 9/0894 (2013.01) [H04L 9/085 (2013.01); H04L 9/14 (2013.01); H04L 63/20 (2013.01); H04L 2209/08 (2013.01); H04L 2209/24 (2013.01)] | 19 Claims |
|
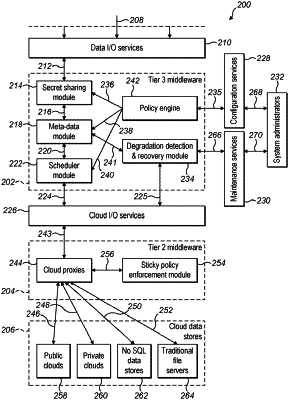
1. A method of securely storing data in a cloud-based vault, the method of securely storing data comprising:
providing, within a secure data storage system, a plurality of secret sharing methods for selection;
receiving input preferences from a user or administrator by a policy module that relate at least to a striping policy;
identifying, by the policy module, a striping policy for storage of the data, in accordance with the input preferences;
splitting the data, by a secret sharing module, into a plurality, N, of secret shares according to a selected one of the plurality of secret sharing methods, a selection of the selected one of the plurality of secret sharing methods being determined by the striping policy, wherein a threshold number, T, of such shares is sufficient to recover the data, where T is less than N,
generating, by a metadata module, metadata associated with the data, the metadata identifying the selected one of the plurality of secret sharing methods and storing the metadata for all the secret shares within the secure data storage system; and
writing, by the secret sharing module, the secret shares to storage including an independent storage and the secure data storage system, the independent storage being implemented outside the secure data storage system, and writing at least some of the secret shares to the independent storage outside the secure data storage system, such that, when at least T shares are retrieved by the secure data storage system, the metadata can be recalled within the secure data storage system to identify the selected one of the plurality of secret sharing methods for recovery of the data,
wherein the input preferences identify a level of resilience and/or a level of security that are utilized to at least enable a user or administrator to select policy attributes that determine values of T and N.
|