| CPC H04L 63/20 (2013.01) [G06F 16/2477 (2019.01); G06F 16/951 (2019.01); H04L 63/1425 (2013.01); H04L 63/1433 (2013.01); H04L 63/1441 (2013.01)] | 6 Claims |
|
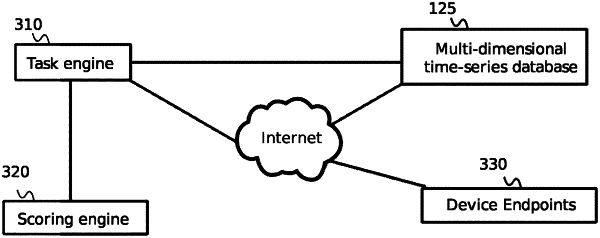
1. A system for self-adjusting cybersecurity analysis and rating based on heterogeneous data and reconnaissance, comprising:
a computing system comprising a memory, a processor, a network interface and a plurality of programming instructions that, when operating on the processor, cause the processor to;
reconnoiter a target network by identifying internet protocol (IP) addresses and subdomains of the target network, verifying domain name system information for each IP address and subdomain of the target network, and computing an Internet reconnaissance score;
collect domain name system leak information by identifying improper network configurations in the IP addresses and subdomains of the target network, and computing a domain name system leak information score;
analyze web applications used by the target network to identify vulnerabilities in the web applications that could allow unauthorized access to the target network, and computing a web application security score;
search social media networks for information of concern related to users identified within the target network, and computing a social network score;
conduct a scan of the IP addresses within the target network for open TCP or UDP ports, and computing an open port score;
identify leaked credentials associated with the target network that are found to be disclosed in previous breach incidents, and computing a credential score;
gather version and update information for hardware and software systems within the boundary of the target network, checking version and update information for the hardware and software systems within the boundary of the target network, and computing a patching frequency score;
identify content of interest contained within the target network, performing an Internet search to identify references to the content of interest, and computing an open-source intelligence score;
assign a weight to each of the computed scores;
combine the weighted scores into a weighted cybersecurity score; and
comparing the weighted cybersecurity score to a score set point; and
recommending changes to network security for the target network to either increase or decrease network security to bring the score into equilibrium with the score set point.
|