| CPC H04L 63/20 (2013.01) [H04L 41/0823 (2013.01); H04L 41/0893 (2013.01); H04L 63/14 (2013.01); H04L 41/0816 (2013.01); H04L 41/145 (2013.01)] | 27 Claims |
|
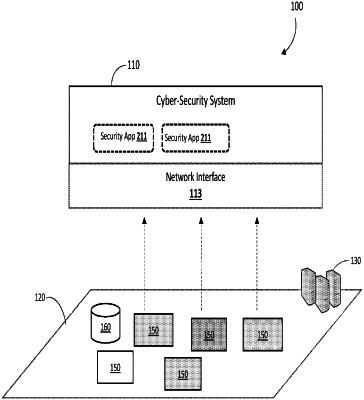
1. A method for optimizing a defense model using available security capabilities, comprising:
obtaining a defense model, wherein the defense model defines a defense behavior with respect to an identified threat;
evaluating available security capabilities deployed in an enterprise environment to determine a plurality of variant security applications implementing the defense model;
determining a quality score for each variant security application of the plurality of variant security applications, the quality score reflecting a level of protection each variant security application offers against the identified threat;
selecting, from the plurality of variant security applications, a variant security application having a highest quality score; and
executing the selected variant security application to respond to the identified threat.
|