| CPC H04L 63/20 (2013.01) [G06F 21/57 (2013.01); G06F 21/572 (2013.01); G06N 20/00 (2019.01); G06F 2221/034 (2013.01)] | 20 Claims |
|
1. A computer-implemented method for enhancing security for a deployment environment comprising a plurality of computing resources, the method comprising:
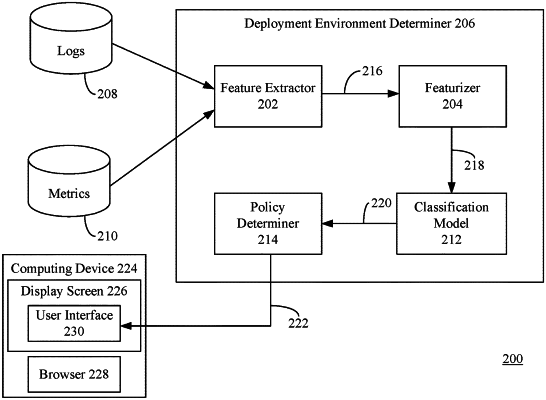
receiving data indicative of a usage of the plurality of computing resources in a particular deployment environment of a plurality of deployment environments, the plurality of deployment environments including a first deployment environment comprising a first stage of development and a second deployment environment comprising a second stage of development the plurality of deployment environments associated with respective stages of development;
generating a feature vector based on the data;
providing the feature vector as input to a machine learning-based classification model that identifies the particular deployment environment as comprising the first stage of development based on the feature vector, the machine learning-based classification model trained based on first past usage data comprising a first deployment environment label corresponding to the first stage of development and second past usage data comprising a second deployment environment label corresponding to the second stage of development; and
determining a security policy from a plurality of security policies that is applicable for the identified deployment environment.
|