| CPC H04L 63/1433 (2013.01) [H04L 63/1441 (2013.01); H04L 63/20 (2013.01)] | 16 Claims |
|
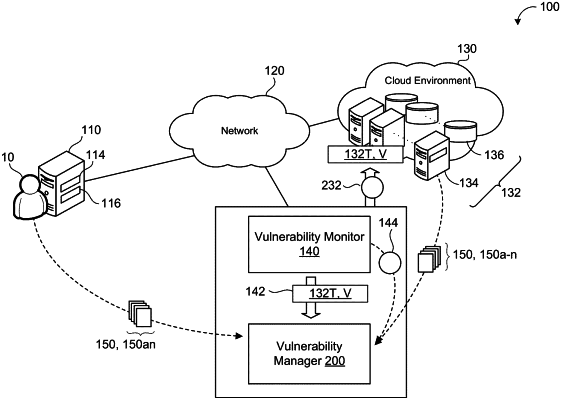
1. A computer-implemented method when executed by data processing hardware causes the data processing hardware to perform operations comprising:
receiving an indication that a target resource comprises a vulnerability, the target resource hosted in a cloud environment and associated with a user of the cloud environment;
determining a first mitigation action to mitigate the vulnerability of the target resource;
transmitting, for display at a client device associated with the user, the first mitigation action;
based on transmitting the first mitigation action, receiving an application indication indicating that the first mitigation action is applied;
in response to receiving the application indication indicating that the first mitigation action is applied, determining that the target resource still comprises the vulnerability;
determining a second mitigation action to mitigate the vulnerability of the target resource, wherein the second mitigation action comprises a reversible mitigation action;
transmitting, for display at the client device associated with the user, the second mitigation action;
based on transmitting the second mitigation action, receiving a second application indication indicating that the second mitigation action is applied;
in response to receiving the second application indication indicating that the second mitigation action is applied, monitoring activity for the target resource;
while monitoring activity for the target resource, determining that the vulnerability of the target resource exists; and
based on determining that the vulnerability of the target resource fails to exist, reversing the second mitigation action.
|