| CPC H04L 63/1425 (2013.01) [G06F 9/455 (2013.01); G06F 9/545 (2013.01); G06F 16/9024 (2019.01); G06F 16/9038 (2019.01); G06F 16/9535 (2019.01); G06F 16/9537 (2019.01); G06F 21/57 (2013.01); H04L 43/045 (2013.01); H04L 43/06 (2013.01); H04L 63/10 (2013.01); H04L 67/306 (2013.01); H04L 67/535 (2022.05); G06F 16/2456 (2019.01)] | 18 Claims |
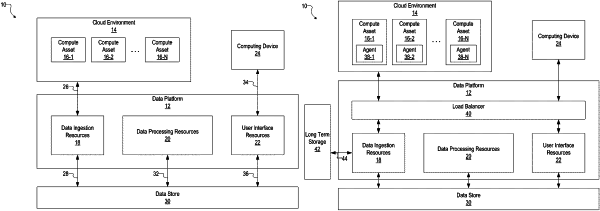
|
1. A method of user-specific data-driven network security, the method comprising:
generating, based on historical activity associated with a user, a trained model for determining whether a network request deviates from normal activity for the user;
receiving, from a user device associated with the user, the network request;
determining, based on the historical activity for the user and the trained model, whether the network request deviates from normal activity for the user; and
initiating, in response to the network request deviating from normal activity for the user, an approval workflow for the network request, wherein the approval workflow comprises one or more user-completable steps that, if completed, cause the network request to he allowed.
|