| CPC H04L 63/1425 (2013.01) [G06F 18/2431 (2023.01); G06N 3/04 (2013.01)] | 20 Claims |
|
1. A system comprising:
a non-transitory computer-readable medium having instructions stored thereon, which, when executed by a processor, cause the system to perform operations comprising:
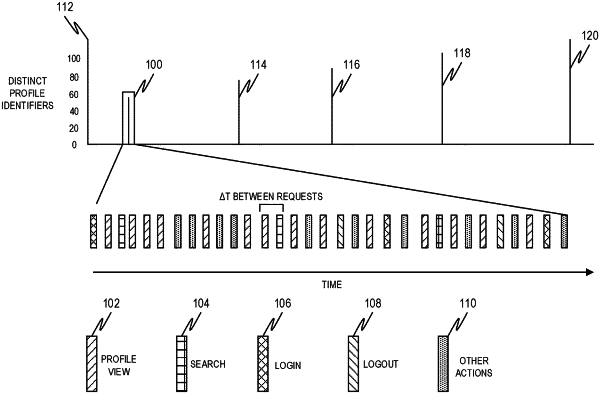
obtaining a first sequence of operations performed by a first account of an online network, the first sequence of operations including a plurality of request paths and an order for operations in the first sequence of operations;
standardizing the plurality of request paths into tokens reflective of operation types of the plurality of request paths;
mapping the tokens to integers reflecting a ranking of a frequency of occurrences of the plurality of request paths in sequences of operations, including the first sequence of operations, performed by a plurality of accounts of the online network;
creating an activity transition matrix for the first account, based on the standardized plurality of request paths and the mapped integers, the activity transition matrix having source request paths on a first axis and destination request paths on a second axis, with values in cells of the activity transition matrix indicative of a frequency of occurrence of a transition by the first account between a corresponding source request path and corresponding destination path during a predetermined time period; and
feeding a label for the activity transition matrix and the activity transition matrix into a machine learning algorithm to train a deep learning machine-learned model to calculate a score indicative of a likelihood that a subsequent activity transition matrix for operations performed by a second account of the online network fed as input to the deep learning machine learned model constitutes abusive operations.
|