| CPC H04L 63/1425 (2013.01) [H04L 63/0876 (2013.01)] | 19 Claims |
|
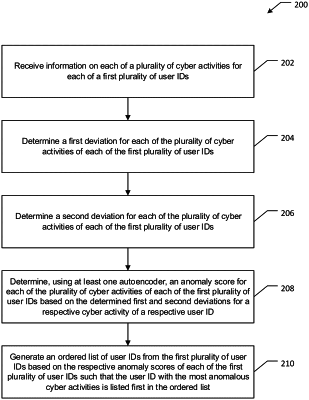
1. A system for detecting anomalous cyber activity comprising: a memory; and a processor in communication with the memory, the processor configured to:
receive information on each of a plurality of cyber activities for each of a first plurality of user IDs, wherein the information is selected from: (1) a quantity of files locally opened by the respective user ID that the respective user ID had never locally opened before, (2) a quantity of files remotely opened by the respective user ID that the respective user ID had never remotely opened before, (3) a quantity of files written locally by the respective user ID that the respective user ID had never written locally before, (4) a quantity of files written remotely by the respective user ID that the respective user ID had never written remotely before, (5) a quantity of local files copied to a remote device that the respective user ID had never copied to a remote device before, and (6) a quantity of remote files copied to a local device that the respective user ID had never copied to a local device before;
determine, for each of the plurality of cyber activities of each of the first plurality of user IDs, a first deviation between the received information on a respective cyber activity for a respective user ID and previously stored information on the respective cyber activity for the respective user ID;
determine, for each of the plurality of cyber activities of each of the first plurality of user IDs, a second deviation between the received information on the respective cyber activity for the respective user ID and previously stored group information on the respective cyber activity for a group including a second plurality of user IDs;
determine, using at least one autoencoder, an anomaly score for each of the plurality of cyber activities of each of the first plurality of user IDs based on the determined first and second deviations for a respective cyber activity of a respective user ID; and
generate an ordered list of user IDs from the first plurality of user IDs based on the respective anomaly scores of each of the first plurality of user IDs such that the user ID with the most anomalous cyber activities is listed first in the ordered list.
|