| CPC H04L 63/1416 (2013.01) [H04L 63/0876 (2013.01); H04L 63/1425 (2013.01); H04L 63/20 (2013.01)] | 1 Claim |
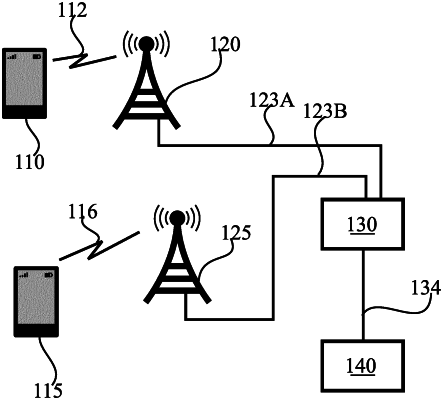
|
1. An apparatus comprising at least one processing core, at least one memory including computer program code, the at least one memory and the computer program code being configured to, with the at least one processing core, cause the apparatus at least to:
establish a user equipment context for a user equipment registered with the apparatus, the user equipment context being associated with an identity of the user equipment;
determine that a plurality of network messages comprising the identity of the user equipment as sender fail a network message integrity process; and
trigger at least one of: 1) sending a paging message to the user equipment, or 2) initiating an authentication process with a sender of the network messages, and deletion the user equipment context as a response to successful completion of the authentication process,
wherein the apparatus is configured to trigger the sending of the paging message, and wherein the apparatus is configured to process a response from the user equipment to the paging message, and where the response passes the network message integrity process, the apparatus is configured to do a non-access stratum re-keying of the user equipment to create a fresh non-access stratum security context from a current context.
|