| CPC H04L 63/1416 (2013.01) [H04L 45/306 (2013.01); H04L 63/1425 (2013.01); H04L 63/1441 (2013.01); H04L 2463/146 (2013.01)] | 17 Claims |
|
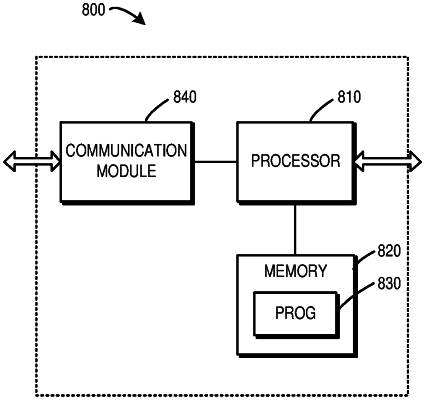
1. A device comprising:
at least one processor; and
at least one memory including computer program code;
the at least one memory and the computer program code configured to, with the at least one processor, cause the device to:
send at an attack tracer to a first service function chain domain of a plurality of service function chain domains, a request for tracing an attack source of an attacking data flow passing through the plurality of the service function chain domains subsequently, the request including flow characteristics of the attacking data flow;
receive, from the first service function chain domain, a first set of results of flow matching based on the flow characteristics; and
identify the attack source in the plurality of the service function chain domains at least in part based on the first set of the results.
|