| CPC H04L 63/102 (2013.01) [H04L 63/0861 (2013.01); H04L 63/105 (2013.01); H04L 2463/082 (2013.01)] | 22 Claims |
|
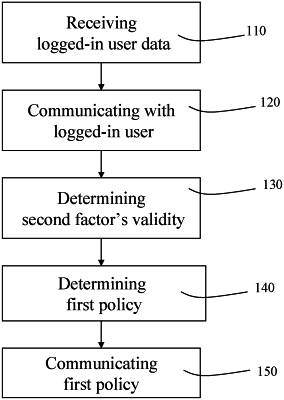
1. A method of multi-factor authentication, the method comprising computer executed steps, the steps comprising:
from a computer of a cloud service, receiving data identifying a user logged-in to the cloud service after being successfully authenticated using a first authentication factor;
communicating with a client device of the user identified by the received data, for receiving a second authentication factor from the user;
determining whether the second authentication factor received from the user is valid;
based on a result of said determining, determining a first user-permission policy for the user; and
communicating the determined first user-permission policy to the computer of the cloud service, for the cloud service to base a restriction of usage of the cloud service by the user on, wherein said determining of the first user-permission policy comprises selecting the first user-permission policy among at least two predefined policies, and wherein a first one of the predefined policies pertains to the second authentication factor being determined to be valid and a second one of the predetermined policies pertains to the second authentication factor not being determined to be valid.
|