| CPC H04L 63/10 (2013.01) [G06F 9/547 (2013.01); H04L 63/1408 (2013.01)] | 20 Claims |
|
1. A method, comprising:
receiving, by a device intermediary to a client and a server, a message from the client with a plurality of fields to execute one or more routines on the server remote from the client;
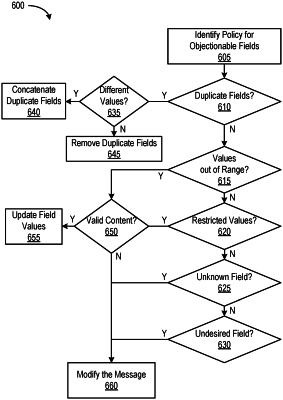
identifying, by the device, duplicate fields in the plurality of fields of the message from the client that, upon execution, reduce server performance;
modifying, by the device instead of the server, the plurality of fields of the message to improve the server performance based at least on the identification of the duplicate fields; and
forwarding, by the device, the modified message to the server.
|