| CPC H04L 63/0435 (2013.01) [G06F 21/335 (2013.01); H04L 9/0825 (2013.01); H04L 9/0841 (2013.01); H04L 9/0869 (2013.01); H04L 9/3263 (2013.01); H04L 63/0442 (2013.01); H04L 63/061 (2013.01); H04L 63/0823 (2013.01); H04L 63/0869 (2013.01); H04L 63/166 (2013.01)] | 15 Claims |
|
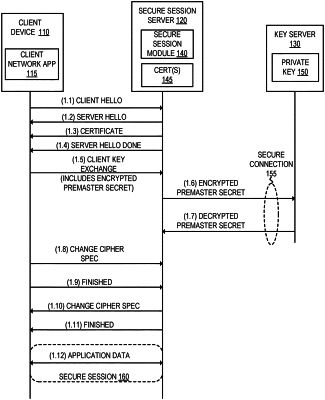
1. A method in a first server for establishing a secure session with a client device where a private key used for the secure session is stored in a second server, the method comprising:
establishing an encrypted connection between the first server and the second server;
receiving a set of one or more messages from the client device for establishing the secure session between the client device and the first server, wherein the set of one or more messages includes information for generation of a premaster secret;
generating a set of cryptographic parameters;
transmitting over the encrypted connection between the first server and the second server and as part of establishing the secure session between the client device and the first server, a request to the second server to use the private key, wherein the request includes the set of cryptographic parameters;
receiving, from the second server over the encrypted connection, a response to the request to use the private key, the response including a signature using the private key over at least the set of cryptographic parameters;
transmitting, to the client device, the set of cryptographic parameters and the signature;
generating, at the first server, the premaster secret using at least part of the generated set of cryptographic parameters and the information for generation of the premaster secret included in the set of one or more messages received from the client device;
generating a master secret using the generated premaster secret; and
generating, using the generated master secret, a set of one or more session keys to be used in the secure session for encrypting and decrypting communication between the client device and the first server.
|