| CPC H04L 63/0428 (2013.01) [G06F 16/13 (2019.01); G06F 17/16 (2013.01); G06F 18/2113 (2023.01); G06F 18/24 (2023.01); G06F 21/6245 (2013.01); G06N 3/04 (2013.01); G06N 3/048 (2023.01); G06N 3/082 (2013.01); G06N 3/098 (2023.01); G06Q 20/401 (2013.01); G06Q 30/0623 (2013.01); H04L 9/008 (2013.01); H04L 9/0625 (2013.01); G06Q 2220/00 (2013.01); H04L 2209/46 (2013.01)] | 18 Claims |
|
1. A method comprising:
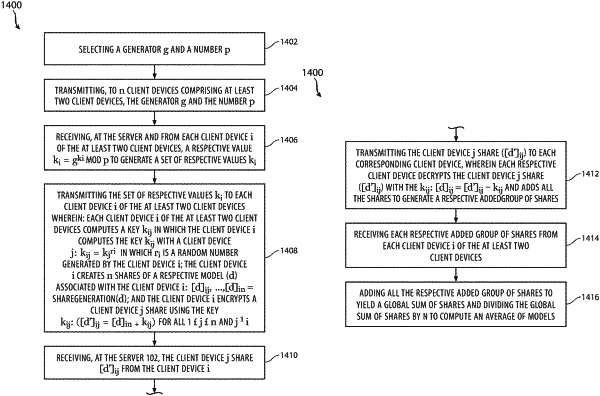
selecting, at a server, Diffie-Hellman numbers comprising: a generatorg and a number p, wherein the generatorg is a public base prime number and the prime number p is a public prime modulus;
transmitting, to at least two client devices, the generator g and the number p;
generating, at each client device i of the at least two client devices, a random number r, and computing a respective key ki using a formula k=gri mod p, wherein mod is a modulus and wherein value of i identifies a respective client device of the at least two client devices;
receiving, at the server and from each client device i of the at least two client devices, the respective ki;
transmitting the respective ki to each client device i of the at least two client devices, wherein:
each client device i of the at least two client devices computes a key kij in which a client device i computes the key kij with a client device j of the at least two client devices: kij=kjri in which ri is the random number generated by the client device i, wherein value of j identifies a different client device of the at least two client devices; and
each client device i creates n shares of a respective model (d) associated with the client device i of the at least two client devices using a s ha reGeneration function: [d]i1. . . [d]in=ShareGeneration(d), wherein n is a value of how many client devices are in the at least two client devices;
computing for each client device i of the at least two client devices a client device j share of the n share of the respective model (d) associated with the client device j of the at least two client devices using a formula: kij: ([d′]ij=[d]ij+seed (kij) for all 1≤j≤n and j≠i to yield an encrypted client device j share ([d′]ij);
receiving, at the server, the encrypted client device j share ([d′]ij) from the client device i of the at least two client devices;
transmitting the encrypted client device j share ([d′]ij) to each corresponding client device of the at least two client devices, wherein each respective client device decrypts the encrypted client device j share ([d′]ij) with the kij: [d]ij=[d′]ij−seed(kij) [[kij]] to yield decrypted client device j shares and adds all the decrypted client device j shares to generate a respective added group of shares;
receiving, at the server, each respective added group of shares from each client device i of the at least two client devices;
adding, at the server, all the respective added group of shares to yield a global sum of shares and dividing the global sum of shares by n to compute using secure multi-party computation an average of models; and
distributing the average of models to each client device i of the at least two client devices.
|