| CPC H04L 63/0428 (2013.01) [H04L 9/085 (2013.01); H04L 9/3268 (2013.01); H04L 63/10 (2013.01); H04L 67/60 (2022.05)] | 6 Claims |
|
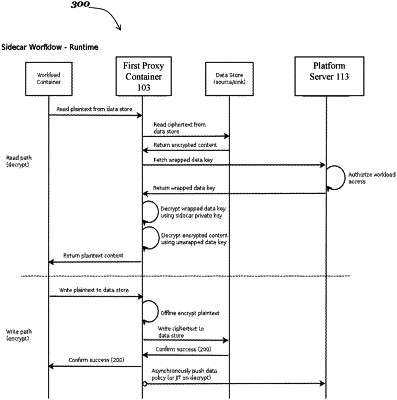
1. A method for securing data access by containerized applications, the method comprising:
intercepting, by a first container executing on a first computing device and associated with a containerized application in a second container executing on the first computing device, a first Internet Protocol (IP) request from the containerized application;
determining, by the first container, that the first IP request is addressed to a second computing device executing a resource that the containerized application is authorized to access;
encrypting, by the first container, a payload portion of the first IP request;
transmitting, by the first container, to the resource, a second IP request with the encrypted payload portion;
receiving, by the first container, from the resource, a response to the second IP request;
requesting, by the first container, from a third computing device, a cryptographic key for decrypting the response to the second IP request;
decrypting, by the first container, with the cryptographic key, a payload portion of the response; and
transmitting, by the first container, to the containerized application, the decrypted payload portion of the response.
|